If your like one of the millions of people using WordPress for their website you have probably dealt with a bruteforce login attack on your site or worse been hacked due to one.
One of the most frustrating things about these attacks is the typical way to address this issue is to either hide your login page via a plugin and custom URL or to add a captcha to the login page. If your like me you despise captchas and how much time is wasted on them.
There is actually a very simple solution to this issue that does not require changing your default login page or even needing a captcha.
Requirements: Static IP or VPN with Static IP
In this example the static IP will be 1.2.3.4. You can actually put multiple IP’s in for the site if you have multiple IP’s for say home office and VPN for when mobile or traveling.
To find your IP can use a site like the below to view your current IP.
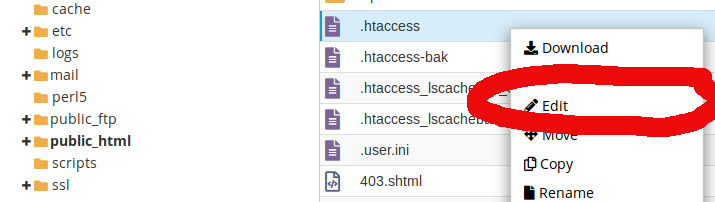
Once you know your IP you will need to note that down and navigate to your control panel or where your WordPress installation is hosting wise. In this example it is going to be inside of cPanel account that houses the WordPress.
Navigate to the main document root for the WordPress install via FTP or the file manager. This will be where the index.php for
/home/username/public_html/.htaccess
Now once
#Redirect all non SSL URLs to use SSL aka HTTPS
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301,NE]
#Deny access to the wp-login page to all except the whitelisted IP's below.
<Files wp-login.php>
order deny,allow
Deny from all
# whitelist home IP address
allow from 1.2.3.4
#whitelist office IP Address
allow from 1.2.3.5
#whitelist vpn IP Address
allow from 1.2.3.6
#commented out rule
#allow from 1.2.3.7
</Files>
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
<files wp-config.php>
order allow,deny
deny from all
</files>You may have other rules below this and that’s fine. If you already have a redirect to SSL rewrite the top one may not be needed. So for our example the entire .htacces basic WordPress file looks like the below. This will prevent anyone from even accessing the login page to attempt a login. This lowers the load on the server instead of waiting for x attempts to fail to ban the IP and deal with the
#Redirect all non SSL URLs to use SSL aka HTTPS
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301,NE]
#Deny access to the wp-login page to all except the whitelisted IP's below.
<Files wp-login.php>
order deny,allow
Deny from all
# whitelist home IP address
allow from 1.2.3.4
#whitelist office IP Address
allow from 1.2.3.5
#whitelist vpn IP Address
allow from 1.2.3.6
#redirect the failed logins to get rickrolled
ErrorDocument 403 https://www.youtube.com/watch?v=dQw4w9WgXcQ
</Files>
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
<files wp-config.php>
order allow,deny
deny from all
</files>
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPressNow that we have the main wp-login page secured we also need to ensure that the admin area which is typically https://yourdomain.tld/wp-admin to also not allow anyone to visit it that is not explicitly whitelisted. We are now going to create a new file called .htaccess in the wp-admin folder. With the same below content whitelisting the desired IP’s and redirecting
/home/username/public_html/wp-admin/.htaccessOrder Deny,Allow Deny from all # whitelist home IP address allow from 1.2.3.4 #whitelist office IP Address allow from 1.2.3.5 #whitelist vpn IP Address allow from 1.2.3.6 ErrorDocument 403 https://www.youtube.com/watch?v=dQw4w9WgXcQ
Once this is done to test you will need to either disconnect from the VPN and test visiting your WordPress login page from an IP that is not whitelisted. If
If you only have a static IP and cannot change it the other method to test is to comment out the rule for the location your currently using so the rule is there but not active. If it works you can use the control panel
#whitelist office IP Address
#allow from 1.2.3.5You may be thinking this is awesome I want to be able to login to my WordPress without weird login URLs or annoying captchas but I don’t have a static IP or VPN. Well your in luck we offer super affordable VPN plans via monthly or super discounted yearly plans in 8 countries and 16 locations. All of them are log-less
Below is a premade .htaccess file for WordPress for our VPN users main .htaccess
#Redirect all non SSL URLs to use SSL aka HTTPS
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301,NE]
#Deny access to the wp-login page to all except the whitelisted IP's below.
<Files wp-login.php>
order deny,allow
Deny from all
# whitelist home IP address
#allow from 1.2.3.4
#whitelist office IP Address
#allow from 1.2.3.5
#whitelist vpn IP Address
#allow from 1.2.3.6
# softy1 NL Amsterdam
Allow from 93.158.203.109
#softy2 NL Amsterdam
Allow from 93.158.203.91
#softy3 US Miami
Allow from 144.202.38.159
#softy4 US Chicago
Allow from 8.12.16.99
#softy5 US New Jersey
Allow from 45.32.6.181
#softy6 US Seattle
Allow from 144.202.93.38
#softy7 US Los Angeles
Allow from 45.76.174.145
#softy8 AU Sydney
Allow from 149.28.162.174
#softy9 JP Tokyo
Allow from 202.182.105.46
#softy10 HK Singapore
Allow from 149.28.151.117
#softy11 FR Paris
Allow from 140.82.54.59
#softy12 DE Frankfurt
Allow from 104.238.167.21
#softy13 UK London
Allow from 45.63.101.64
#Softy14 NL Amsterdam
Allow from 93.158.203.100
#softy15 NL Amsterdam
Allow from 93.158.203.112
#softy16 CA Toronto
Allow from 155.138.147.206
</Files>
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
<files wp-config.php>
order allow,deny
deny from all
</files>
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPressThe below is the .htaccess file to use in the WordPress admin folder. Please note this same method will work for any CMS to protect an admin folder like Prestashop, Opencart, Magento, WHMCS, and etc… so pretty amazing way to secure these areas with very little effort.
Order Deny,Allow Deny from all # whitelist home IP address #allow from 1.2.3.4 #whitelist office IP Address #allow from 1.2.3.5 #whitelist vpn IP Address #allow from 1.2.3.6 # softy1 NL Amsterdam Allow from 93.158.203.109 #softy2 NL Amsterdam Allow from 93.158.203.91 #softy3 US Miami Allow from 144.202.38.159 #softy4 US Chicago Allow from 8.12.16.99 #softy5 US New Jersey Allow from 45.32.6.181 #softy6 US Seattle Allow from 144.202.93.38 #softy7 US Los Angeles Allow from 45.76.174.145 #softy8 AU Sydney Allow from 149.28.162.174 #softy9 JP Tokyo Allow from 202.182.105.46 #softy10 HK Singapore Allow from 149.28.151.117 #softy11 FR Paris Allow from 140.82.54.59 #softy12 DE Frankfurt Allow from 104.238.167.21 #softy13 UK London Allow from 45.63.101.64 #Softy14 NL Amsterdam Allow from 93.158.203.100 #softy15 NL Amsterdam Allow from 93.158.203.112 #softy16 CA Toronto Allow from 155.138.147.206 ErrorDocument 403 https://www.youtube.com/watch?v=dQw4w9WgXcQ
Please note if you accidentally block yourself or forget to whitelist a new location. Login to your control panel or through FTP/SFTP to where your WordPress files are and just comment out the deny all line in the .htaccess files. When you’re done with WordPress uncomment it so it’s active again.
Category:ProxySecuritywhmcsWordpress
